Mar 21, · With this dissertation, I seek to provide an in-depth understanding of the role developing country governments can play in accelerating ICT adoption. By analyzing the institutional, technology, and market factors, this study seeks to provide a solid foundation for examining the design and implementation of successful ICT strategies the authenticity of their digital documents, similar to that enjoyed by the print format, and to preserve the integrity of the information. While digital provision of government information has many benefits, the authenticity of content provided in this format must be safeguarded and its preservation blogger.com: Timothy L. Coggins Authentication protocols are very common mechanisms to confirm the legitimacy of someone’s or something’s identity in digital and physical systems. This thesis presents a new and robust authentication method based on users’ multiple devices. Due to the popularity of mobile devices, users are becoming more likely to have more than one device (e.g., smartwatch, smartphone, laptop, tablet Author: Cagri Cetin
Authentication | blogger.com
Deposit your masters paper, project or other capstone work. Theses will be sent to the CDR automatically via ProQuest and do not need to be deposited.
Deposit dissertation government digital document authentication peer-reviewed article or book chapter. Deposit a complete issue of a scholarly journal, newsletter or book. Deposit scholarly works such as posters, presentations, conference papers or white papers.
Skip to Content. Toggle navigation Carolina Digital Repository. Help Contact Us Login. Browse Everything Collections Departments Deposit Go. Technology adoption and the role of government: examining the national information and communication technology policies in developing countries Public Deposited. You do not have access to any existing collections. You may create a new collection.
Downloadable Content Download PDF. Citation Request Accessible Version, dissertation government digital document authentication. MLA Maynard, dissertation government digital document authentication, Nicholas C. Technology Adoption and the Role of Government: Examining the National Information and Communication Technology Policies In Developing Countries. APA Maynard, N. Technology adoption and the role of government: examining the national information and communication technology policies in developing countries.
Chicago Maynard, Nicholas C. Share on Facebook. Share on Twitter. Last Modified March 21, Creator Maynard, Nicholas C. Affiliation: College of Arts and Sciences, dissertation government digital document authentication, Department of Public Policy Abstract With this dissertation, I seek to provide an in-depth understanding of the role developing country governments can play dissertation government digital document authentication accelerating ICT adoption.
By analyzing the institutional, technology, and market factors, this study seeks to provide a solid foundation for examining the design and implementation of successful ICT strategies. This research uses a combination of empirical and case study evidence to highlight the key challenges of reforming ICT policies and institutions within developing countries.
Further, this study clarifies the role of national governments in sponsoring and promoting ICT access and usage.
Currently, there is a growing disparity between those developing countries that have successfully integrated ICTs into their economies and those that have not. Many developing countries have created national ICT policies and institutions to dissertation government digital document authentication technological deployment with the goal of supporting productivity gains and new business development. However, for many countries, these initiatives have not translated to higher levels of ICT adoption or improved economic development, dissertation government digital document authentication.
This has left developing country governments with a great deal of uncertainty over what policies to implement and which initiatives to fund. The case study analysis within this study has identified several key barriers to accelerating ICT adoption within developing countries.
These barriers include a lack of affordable services, low levels of local expertise, and poor infrastructure, which combine to prevent latecomer countries from developing self-sustaining demand within the sector. Those developing countries with accelerated growth in their ICT sectors tend to have institutions capable of adapting their policies and institutions to the rapid pace technological and market evolution.
This is also confirmed by my empirical research, which showed a positive and significant relationship between ICT institutions and levels of ICT adoption, while controlling for economic and social factors. In contrast, those developing country governments without an active role in regulating ICT competition or supporting ICT adoption and innovation have been unable to sustain rapid growth of their sector.
Degree granting institution University of North Carolina at Chapel Hill Language English Access Open access. Parents: This work has no parents. Items Thumbnail Title Date Uploaded Visibility Actions Technology adoption and the role of government : examining the national information and communication technology policies in developing countries Public Press to Select an action Download.
Tweet Share. Master's Papers Deposit your masters paper, project or other capstone work. Scholarly Articles and Book Chapters Deposit a peer-reviewed article or book chapter.
Undergraduate Honors Theses Deposit your senior honors thesis. Scholarly Journal, Newsletter or Book Deposit a complete issue of a scholarly journal, newsletter or book. Datasets Deposit your dataset.
Datasets may be associated with an article or deposited separately. Multimedia Deposit your 3D objects, audio, images or video. Poster, Presentation or Paper Deposit scholarly works such as posters, presentations, conference papers or white papers.
Technology adoption and the role of government : examining the national information and communication technology policies in developing countries. Press to Select an action Download.
GDPR explained: How the new data protection act could change your life
, time: 5:40Certificate authentication - Department of Information Technology, KRG

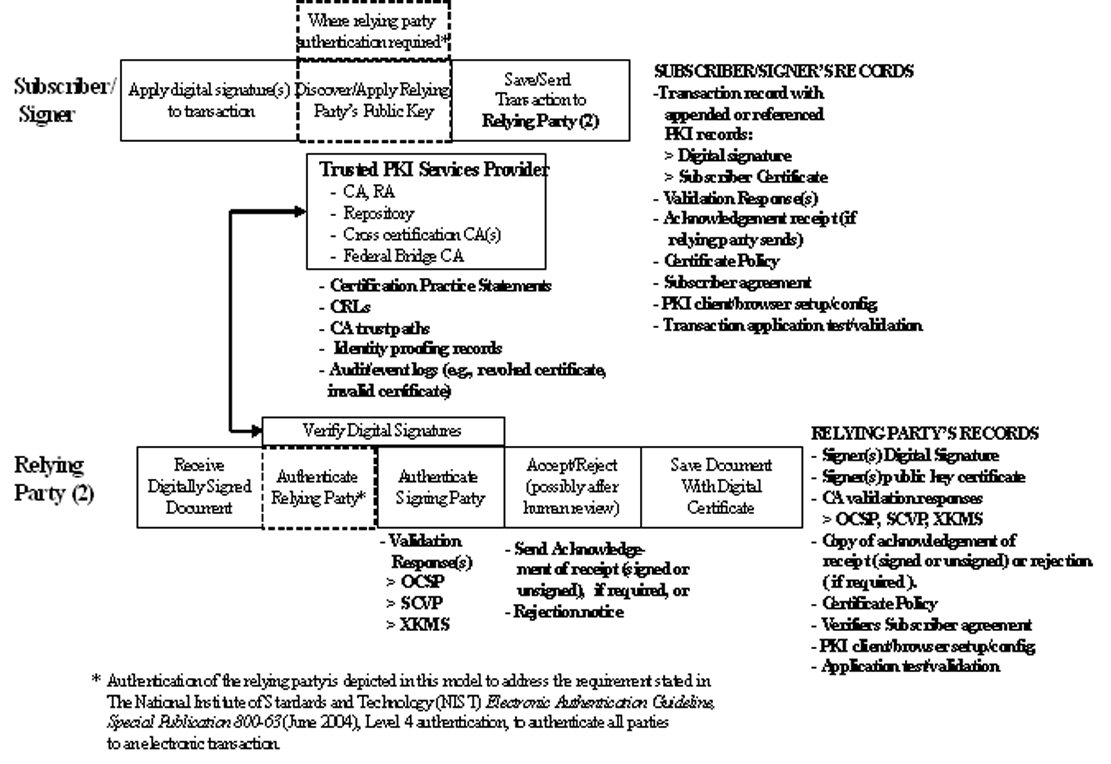
A signatory signs a digital document using a combination of the public and private key, and this document can then be verified using the public key that is publicly available to everyone. Authentication: the source of a digital document Continue reading Software. Organization. Dissertation Proposal. Cover Letter. Dissertation Dissertation Government Digital Document Authentication, how to write the final chapter of a dissertation, custom dissertation results ghostwriting site online, example of semi narrative essay/10() Authentication protocols are very common mechanisms to confirm the legitimacy of someone’s or something’s identity in digital and physical systems. This thesis presents a new and robust authentication method based on users’ multiple devices. Due to the popularity of mobile devices, users are becoming more likely to have more than one device (e.g., smartwatch, smartphone, laptop, tablet Author: Cagri Cetin
No comments:
Post a Comment